A ransomware called JungleSec is infecting victims through unsecured IPMI (Intelligent Platform Management Interface) cards since early November.
When originally reported in early November, victims were seen using Windows, Linux, and Mac, but there was no indication as to how they were being infected. Since then, BleepingComputer has spoken to multiple victims whose Linux servers were infected with the JungleSec Ransomware and they all stated the same thing; they were infected through unsecured IPMI devices.
IPMI is a management interface built into server motherboards or installed as an add-on card that allow administrators to remotely manage the computer, power on and off the computer, get system information, and get access to a KVM that gives you remote console access.
This is extremely useful for managing servers, especially when renting servers from another company at a remote collocation center. If the IPMI interface is not properly configured, though, it could allow attackers to remotely connect to and take control of your servers using default credentials.
Installing JungleSec through IPMI
In conversations between BleepingComputer and two victims it was discovered that attackers installed the JungleSec ransomware through the server's IPMI interface. In one case, the IPMI interface was using the default manufacturer passwords. The other victim stated that the Admin user was disabled, but the attacker was still able to gain access through possible vulnerabilities.
Once the user gained access to the servers, which in both of these cases were Linux, the attackers would reboot the computer into single user mode in order to gain root access. Once in single user mode, they downloaded and compiled the ccrypt encryption program.
According to one of the victims who posted on Twitter, once ccrypt was downloaded, the attackers would manually execute it to encrypt a victim's files. The command used by the attackers is similar to:
/usr/local/bin/ccrypt -e -f -S junglesec@anonymousspeechcom -s -r -l /var/lib
Entering this command would prompt the attacker to enter a password that would then be used to encrypt the files.
One of the victims, Alex Negulescu told BleepingComputer that the attackers would then cause a message to be displayed when performing the sudo command that stated the victim should read the ENCRYPTED.md file.
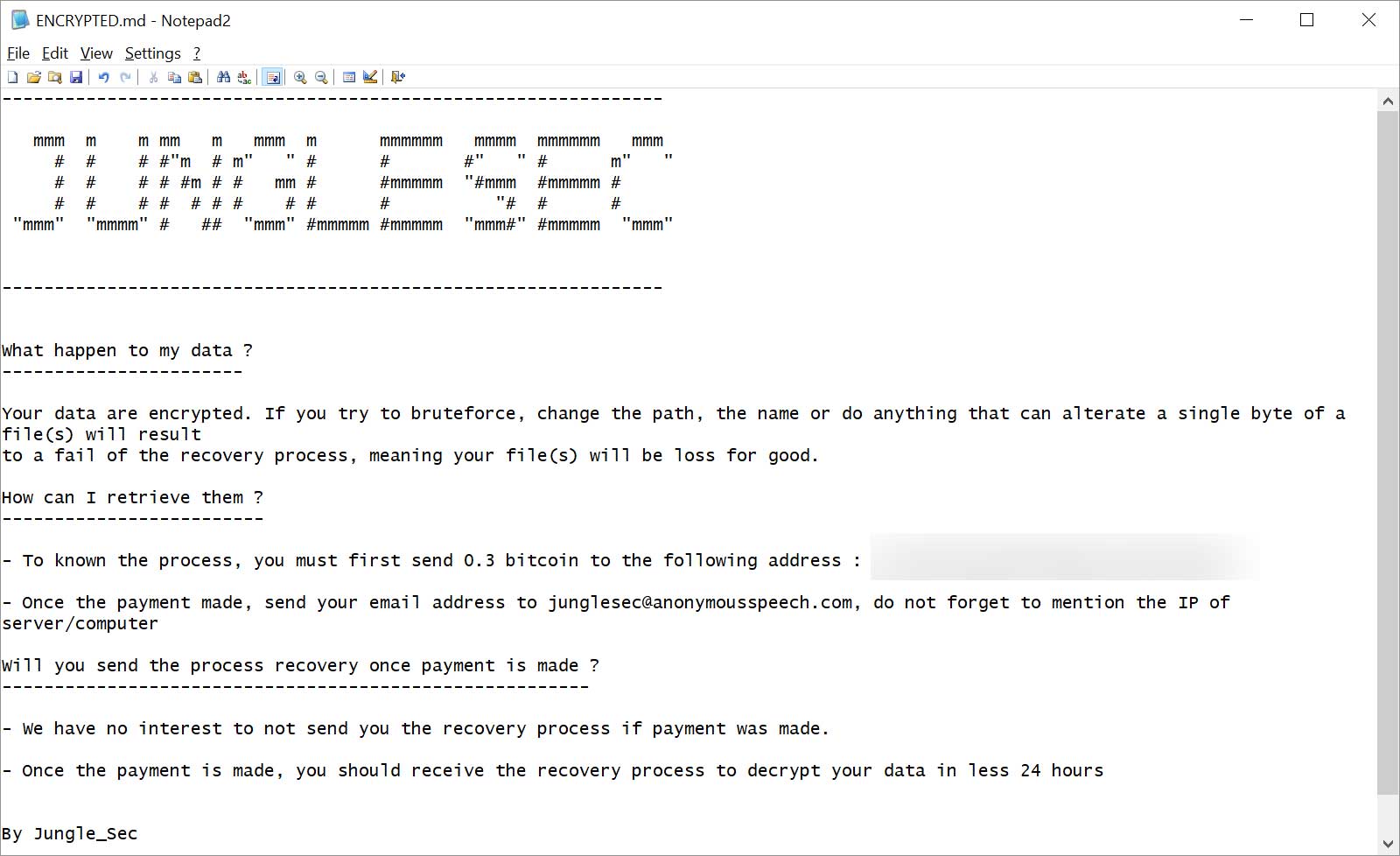
The ENCRYPTED.md file is the ransom note for the JungleSec Ransomware and is shown below. This ransom note contains instructions to contact the attacker at junglesec@anonymousspeech.com and to send .3 bitcoins to the enclosed bitcoin address in order to get the files back.
Another victim who goes by the name pupper on Twitter told BleepingComputer that the attacker also searched for and mounted virtual machine disks, but had trouble properly encrypting them
"They mounted all the qemu/kvm disks so they could also encrypt all the files inside VMs. However the hacker never managed to infect more then 1 useless home directory and 1 KVM machine though."
Pupper also told us that the attackers left behind a backdoor that listens on TCP port 64321 and created a firewall rule to allow access to this port. It is not known what program was installed to be used as a backdoor.
-A INPUT -p tcp -m tcp --dport 64321 -j ACCEPT
Last, but not least, there are multiple reports of victims paying the ransomware, but not receiving a response from the attacker and have not been able to recover their data. While the general rule is to not pay a ransom as it only encourages further ransomware development, this is a another reason not to do so.
How to secure IPMI interfaces
IPMI interfaces are either incorporated directly into server motherboards or through add-on cards that are installed into a computer. If you are using an IPMI interface, it is important that they are properly secured so that attackers cannot utilize them to compromise a server.
The first step in securing an IPMI interface is to change the default password. Many of these cards will come from the manufacturer with default passwords like Admin/Admin, so it is imperative that the password is immediately changed.
Administrators should also configure ACLs that allow only certain IP addresses to access the IPMI interface. In addition, IPMI interfaces should be configured to only listen on an internal IP address so that it is only accessible by local admins or through a VPN connection.
Another tip provided by Negulescu and not necessarily specific to IPMI interfaces, is to add a password to the GRUB bootloader. Doing so will make it more difficult, if not impossible, to reboot into single user mode from the IPMI remote console.
IOCs
Associated File Names:
ENCRYPTED.md
key.txt
Associated Email addresses:
junglesec@anonymousspeech.com
Ransom Note Text:
---------------------------------------------------------------
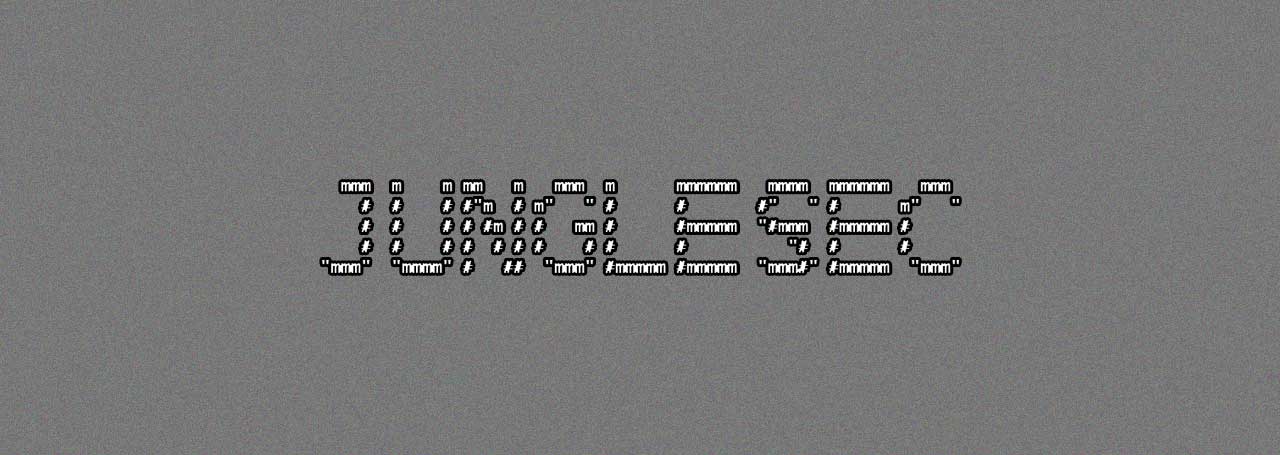
mmm m m mm m mmm m mmmmmm mmmm mmmmmm mmm
# # # #"m # m" " # # #" " # m" "
# # # # #m # # mm # #mmmmm "#mmm #mmmmm #
# # # # # # # # # # "# # #
"mmm" "mmmm" # ## "mmm" #mmmmm #mmmmm "mmm#" #mmmmm "mmm"
---------------------------------------------------------------
What happen to my data ?
-----------------------
Your data are encrypted. If you try to bruteforce, change the path, the name or do anything that can alterate a single byte of a file(s) will result
to a fail of the recovery process, meaning your file(s) will be loss for good.
How can I retrieve them ?
-------------------------
- To known the process, you must first send 0.3 bitcoin to the following address : [bitcoin_address]
- Once the payment made, send your email address to junglesec@anonymousspeech.com, do not forget to mention the IP of server/computer
Will you send the process recovery once payment is made ?
--------------------------------------------------------
- We have no interest to not send you the recovery process if payment was made.
- Once the payment is made, you should receive the recovery process to decrypt your data in less 24 hours
By Jungle_Sec



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now