Discover Microsoft Copilot for Security. Protect your organization at machine speed and scale with generative AI.

Insights every organization needs to defend themselves
Our technologies connect billions of customers around the world. This allows us to aggregate security data to understand the scope and scale of digital threats around the globe. With such diverse threats coming from so many sources, it is incredibly difficult for our customers to anticipate when and where they might be attacked and how to effectively defend themselves.
That is why we share our unique insights on how the digital threat landscape is evolving and the crucial actions that can be taken now to manage the risks.
Our unique vantage point
43 trillion
We use sophisticated data analytics and AI algorithms to better understand and protect against digital threats and cybercriminal activity.
70 billion
We blocked more than 70 billion email and identity threat attacks last year alone.
10,000
domains removed
To date, Microsoft removed more than 10,000 domains used by cybercriminals and 600 used by nation state actors.
8,500+
security and threat intelligence experts
Engineers, researchers, data scientists, threat hunters, geopolitical analysts, investigators, frontline responders, and cybersecurity experts across 77 countries.
Five critical focus areas

State of Cybercrime
Cybercrime continues to rise, driven by increases in both random and targeted attacks. Attack methods have evolved to create increasingly diverse threats.

Nation State Threats
Nation state actors are launching increasingly sophisticated cyberattacks to evade detection and further their strategic priorities.

Devices and Infrastructure
As organizations harness advances in computing capability and entities digitize to thrive, the attack surface of the digital world is exponentially increasing.

Cyber Influence Operations
Today’s foreign influence operations utilize new methods and technologies, making their campaigns designed to erode trust more efficient and effective.

Cyber Resilience
As threats in the cyber landscape increase, building cyber resilience into the fabric of the organization is as crucial as financial and operational resilience.
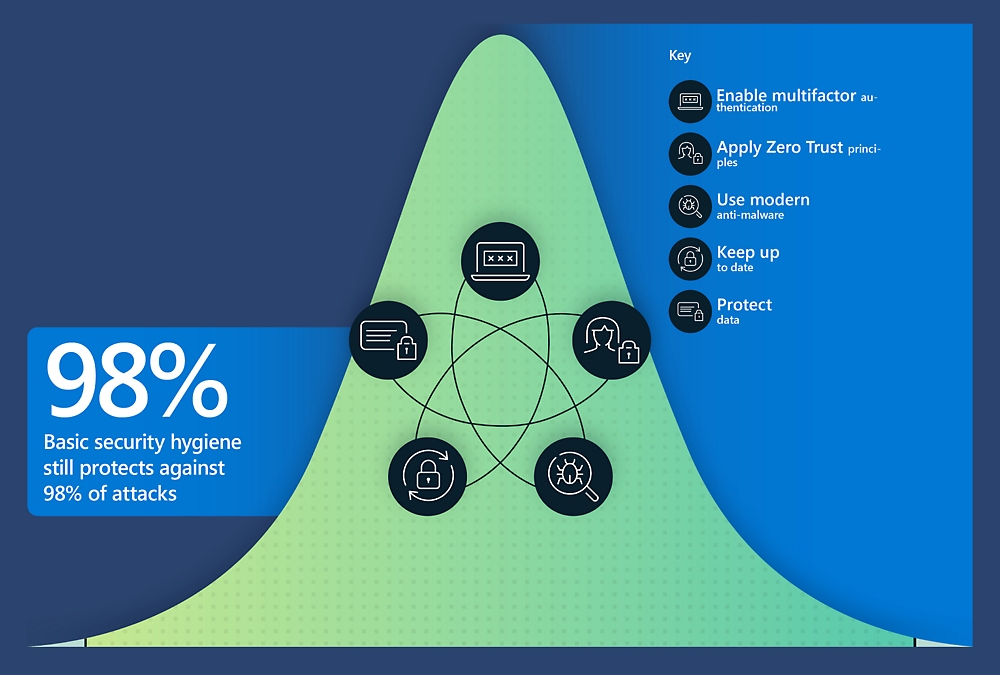
Why the cyber resilience bell curve matters
There is an increasing sense of urgency to adopt these minimum standards for greater resiliency to the rising level of threats in the digital ecosystem.


Follow Microsoft